In 2021, I wrote an article on how to set up mutual TLS (mTLS) and, at the time, AWS Application Load Balancer (ALB) didn’t support mTLS. I remember reaching out to the AWS team and they informed me that it was on their roadmap. So, I moved forward with configuring mTLS on AWS Network Load Balancer (NLB) instead.
Fast forward to now, AWS ALB now supports mTLS 😊.
Mutual TLS on AWS
AWS ALB now supports mTLS, offering a secure way to authenticate clients on both sides while establishing TLS-encrypted connections.
Mutual TLS is an extension of the regular SSL/TLS protocol, where both the client and the server authenticate each other using X.509 certificates. This ensures a higher level of trust compared to traditional TLS, where only the server is authenticated.
To learn more about Mutual TLS, please refer to our article where we delve into Mutual TLS authentication in depth.
Overview of Application Load Balancer
In the world of AWS, the Application Load Balancer (ALB) is a powerful component that sits within the Elastic Load Balancing service designed specifically for HTTP and HTTPS traffic. . As a brief introduction, ALB automatically distributes incoming traffic across multiple targets, such as EC2 instances and containers, to optimize performance and maintain high availability in cloud environments.
Benefits of Using ALB
Using AWS Application Load Balancer (ALB) offers several benefits, including:
- High Availability: ALB automatically distributes incoming traffic across multiple targets in different availability zones, ensuring high availability and fault tolerance.
- Advanced Routing: ALB supports advanced routing capabilities, allowing traffic to be routed based on the content of the request. This enables more sophisticated load balancing and routing scenarios.
- SSL/TLS Offloading: ALB can terminate SSL/TLS connections, offloading the decryption process from the backend servers and reducing their workload.
- Containerized Applications Support: ALB seamlessly integrates with containerized applications, providing load balancing and routing for container-based workloads.
- WebSockets and HTTP/2 Support: ALB supports WebSockets and HTTP/2, enabling efficient communication for modern web applications.
- Security Features: ALB integrates with AWS Web Application Firewall (WAF) to provide enhanced security and protection against common web exploits.
- Content-Based Routing: ALB allows routing decisions to be based on the content of the request, enabling more granular control over traffic distribution.
- Centralized SSL Certificate Management: ALB supports centralized management of SSL certificates, simplifying the management of secure connections for multiple applications.
- Target Group Health Checks: ALB performs health checks on targets to ensure that traffic is only routed to healthy instances, improving overall application reliability.
- Access Logs: ALB provides detailed access logs, which can be used for monitoring, troubleshooting, and analysis of traffic patterns.
These benefits make ALB a versatile and powerful tool for managing and optimizing the distribution of application traffic within an AWS environment.
How ALB Implements mTLS
Mutual TLS on ALB provides two different options for validating the X.509 client certificates:
Passthrough mode: In this mode, ALB sends the entire client certificate chain to the target using HTTP headers. This enables us to implement relevant authentication and authorization logic in your application.
Verify mode: In this mode, we can offload the X.509 client certificate authentication to the ALB while negotiating TLS connections. We can authenticate clients from any third-party Certificate Authority (CA) or the AWS Private Certificate Authority (PCA). We can also optionally enable revocation checks to restrict access for compromised client certificates.
In both modes, you can also optionally enable revocation checks to restrict access for compromised client certificates. This further strengthens the security of your application.
Implementing mTLS on AWS ALB offers a more secure way to protect the applications by authenticating both the client and the server using X.509 certificates. With the choice between passthrough and verify mode, we can easily tailor mTLS implementation to suit application’s specific requirements and ensure a higher level of trust between all parties involved in the communication process.
Configuring mTLS on ALB (Step-by-step guide with illustrations)
Prerequisites for Configuration
Before getting started with configuring mTLS on AWS Application Load Balancer (ALB), ensure that you are using the supported TLS versions (such as TLS 1.2 or TLS 1.3) and obtain valid X.509v3 SSL certificates.
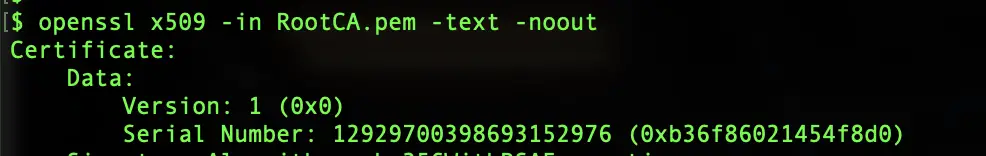
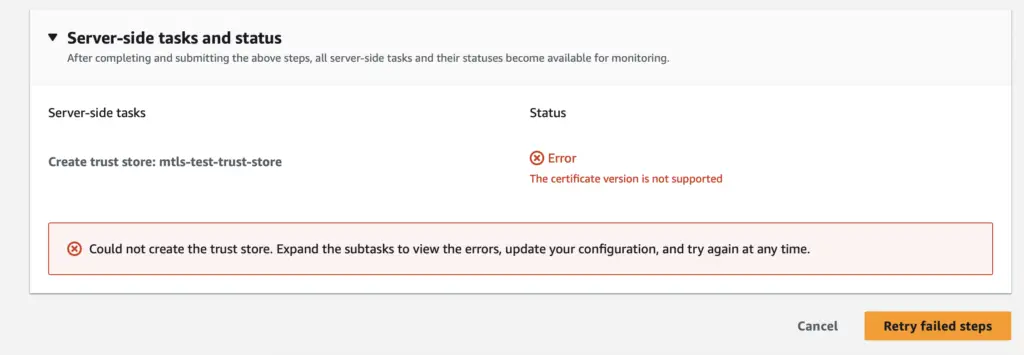
Note: X.509v1 client certificates are not supported.
If you use an x509v1 certificate, you may encounter an error when interacting with the truststore.
Application Load Balancers support the following for certificates used with mutual TLS authentication:
- Supported certificate: X.509v3
- Supported public keys: RSA 2K – 8K or ECDSA secp256r1, secp384r1, secp521r1
- Supported signature algorithms: SHA256, 384, 512 with RSA/SHA256, 384, 512 with EC/SHA256,384,512 hash with RSASSA-PSS with MGF1
For a smooth configuration process, it is advisable to have a good understanding of AWS Certificate Manager (ACM), AWS Identity and Access Management (IAM), and Listener configurations.
Setting Up Listeners for mTLS
To set up listeners for mTLS on ALB, begin by creating a new listener that accepts HTTPS traffic. You will then need to configure this listener to authenticate clients using their X.509 certificates.
Using AWS Certificate Manager
AWS Certificate Manager (ACM) plays a pivotal role in the mTLS configuration process. With ACM, you can easily obtain, manage and deploy public and private SSL/TLS certificates for secure communication between your clients and ALB.
Configuring mTLS on ALB is achievable with a proper understanding of the AWS services involved and the right set of configurations. With the right steps in place, your ALB will be able to authenticate client certificates securely and reliably.
To use ACM, you will have to request or import an SSL/TLS certificate and choose it while creating an HTTPS listener. For mTLS, the client certificates will also be verified against the certificate authority that issued them.
Integrating IAM with Certificate Management
In addition to using ACM for certificates, you can also leverage AWS Identity and Access Management (IAM) for managing and using your SSL/TLS certificates. This helps manage access and permissions to your certificates across different services on AWS.
Ensuring proper IAM access control allows only authorized users and resources to access your ALB and perform the required actions.
Each certificate authority (CA) certificate bundle is uploaded as a batch by Application Load Balancers. Individual certificate uploads are not supported. To include new certificates, you are required to upload the certificate bundle file.
To import the certificate into the ACM; Locate AWS Certificate Manager and choose Import
Then provide the necessary certificate details and click on Next
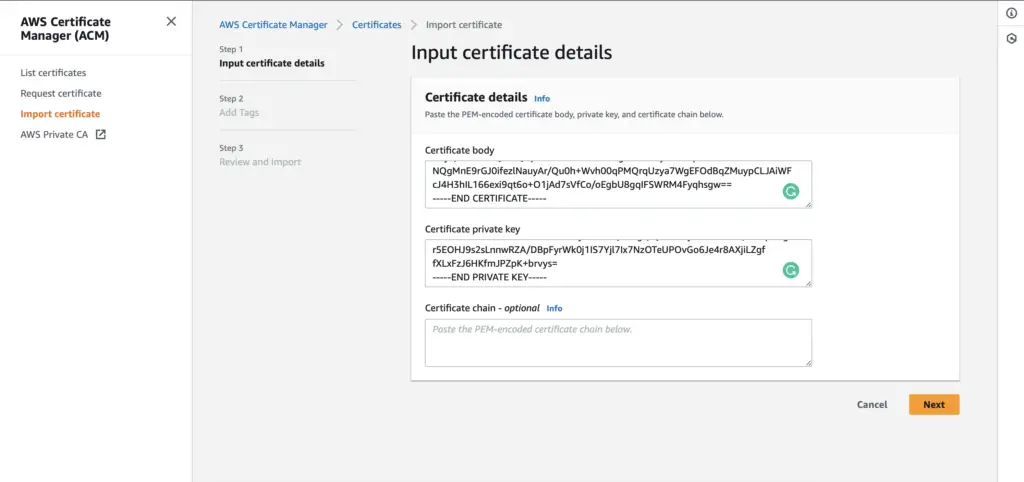
Review the details and click on Import
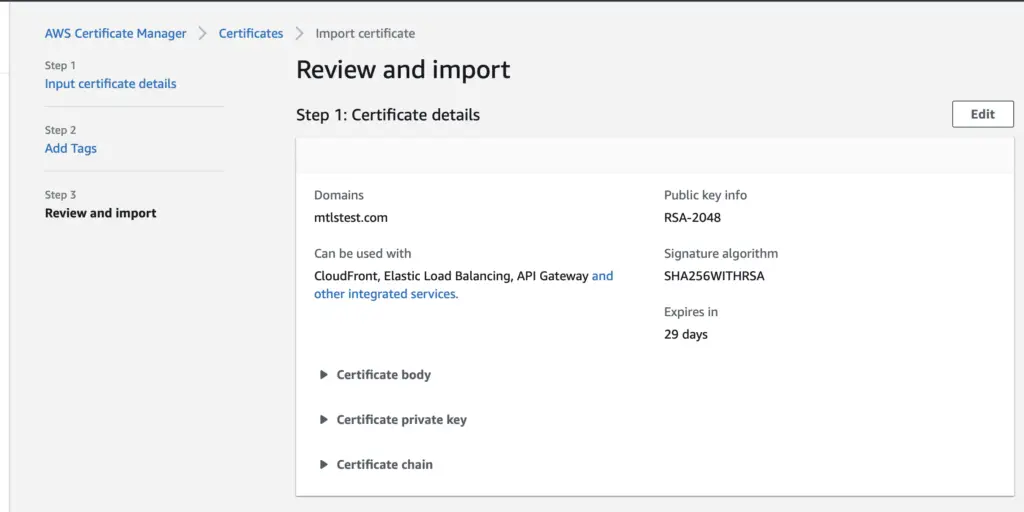
Verify the Import
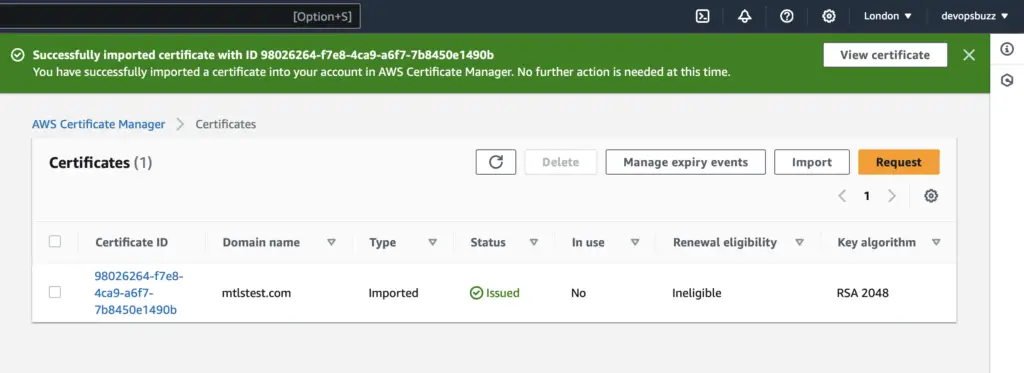
Application should be up and running
To configure mutual TLS (mTLS) on an Application Load Balancer (ALB), you need to ensure that your application is up and running and accessible.
Additionally, the target groups associated with the ALB should be properly configured to direct traffic to the respective instances.
Choosing the right option for mTLS
You now get an option to enable Mutual Authentication with 2 modes in ‘Client certificate handling’ section
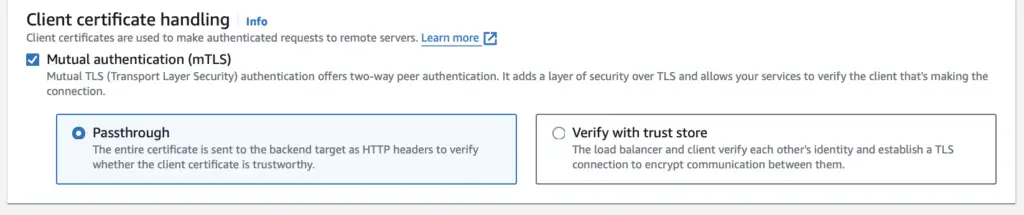
To enable Mutual TLS passthrough mode, simply set up the listener to accept certificates from clients. In this mode, the Application Load Balancer forwards the complete client certificate chain to the target via HTTP headers.
This allows you to establish authentication and authorization mechanisms within your application. For additional details, refer to the documentation Create an HTTPS listener for your Application Load Balancer.
Let’s try to configure mTLS for ALB with the Passthrough option
Locate ‘Load Balancer’ service and Choose Application Load Balancer
Provide the Basic details; such as Load balancer name, IP address type, VPC, Subnets, Security Groups, etc
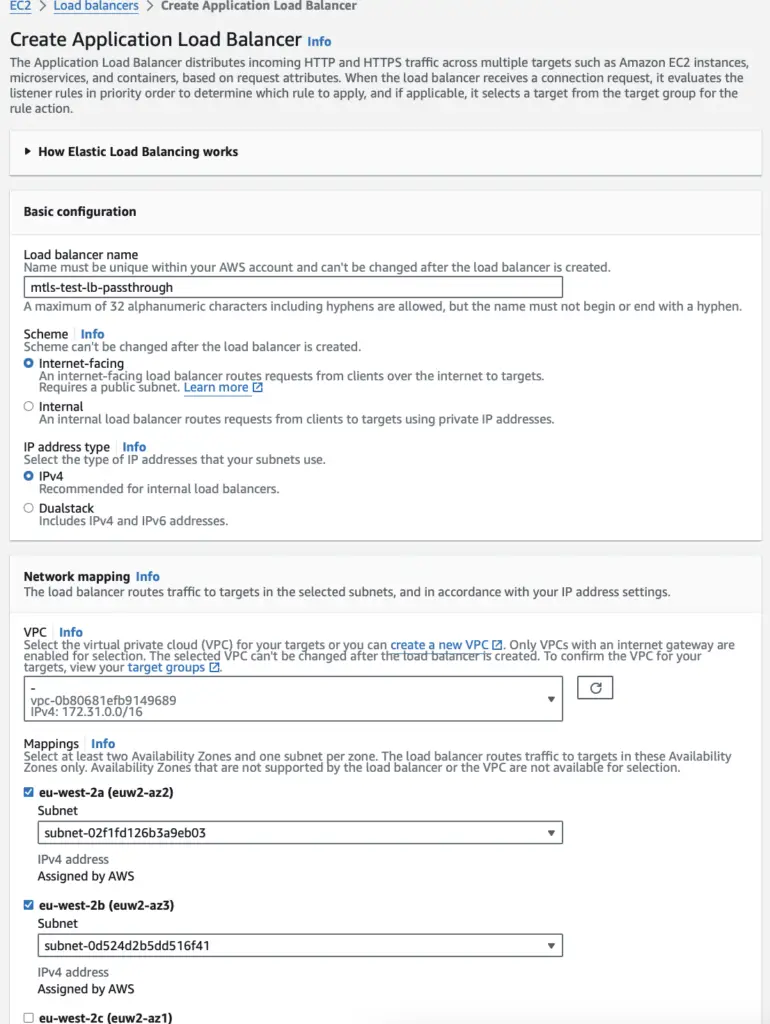
And then Create/Add a HTTPS Listener
When you choose HTTPS Listener, a new option will be enabled to configure ‘Secure listener settings‘
Choose the appropriate Security policy, Certificate and choose Passthrough when you enable Mutual authentication (mTLS)
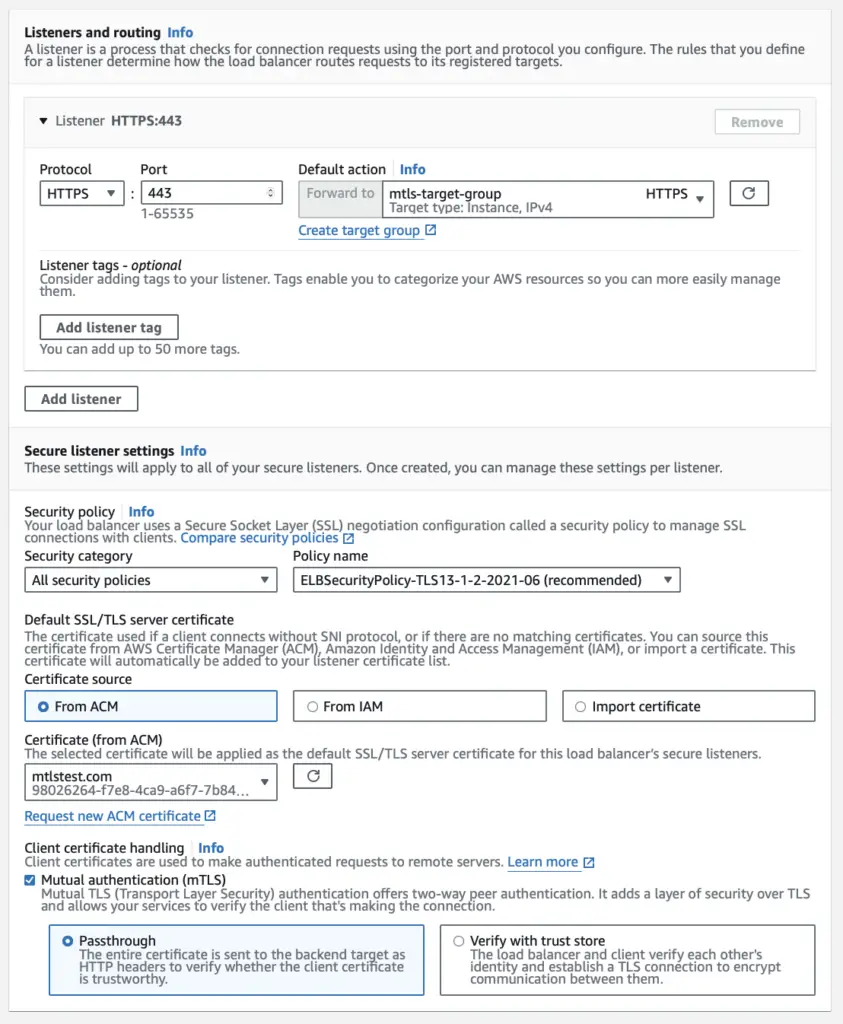
Click on Create Load Balancer
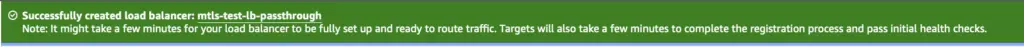
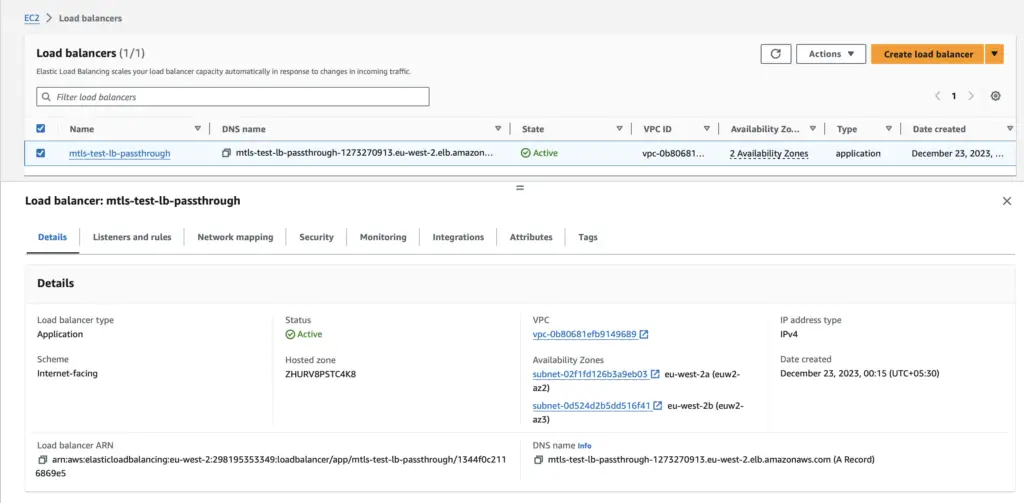
Verify the newly created Load Balancer details
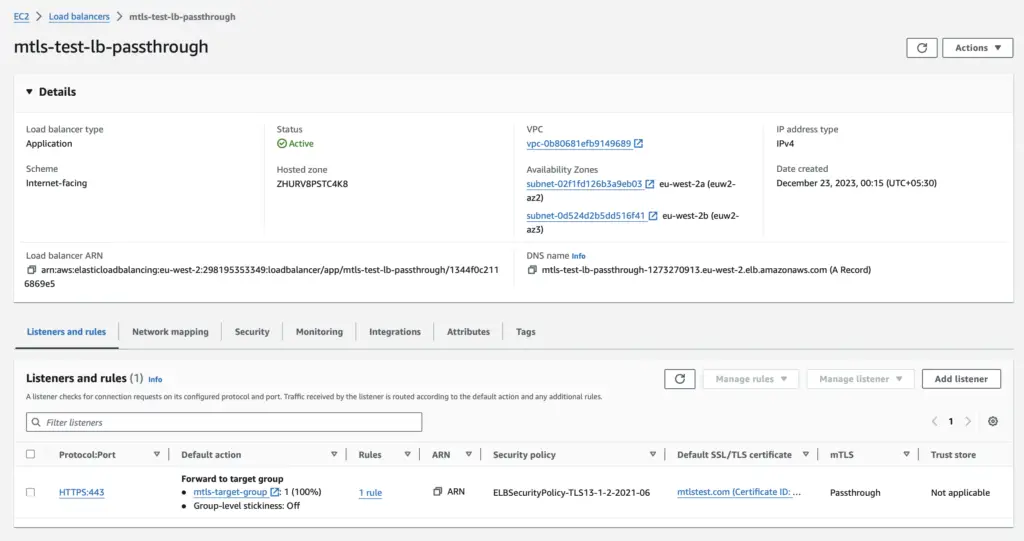
And verify Listeners and Rules
Whereas, when employing Mutual TLS in verify mode, the Application Load Balancer conducts X.509 client certificate authentication during TLS connection negotiations.
To implement mutual TLS verify mode, we need to follow a different process that involves additional configuration steps.
Start with uploading the Certificate Authority bundle in S3 bucket and then create a new trust store resource
Locate the S3 service and create the bucket to store the CA certificate, and PEM-formatted file and upload the certificates
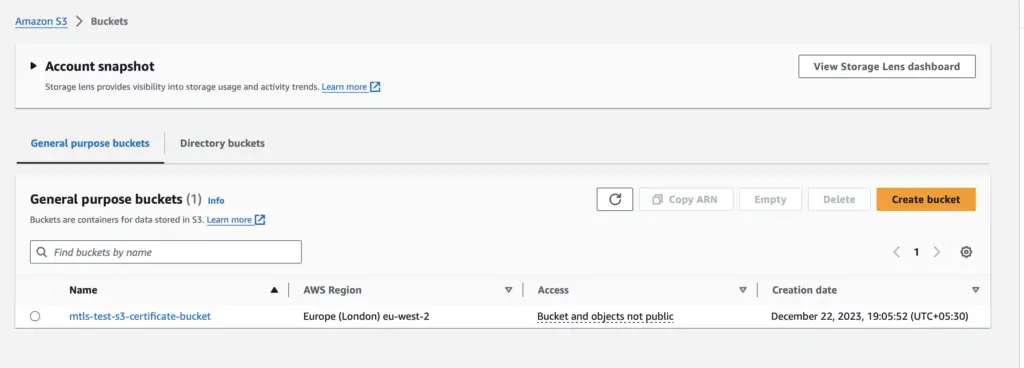
Select a PEM-formatted CA certificate bundle and, if desired, include Certificate Revocation Lists (CRLs) from your Amazon S3 bucket. A CA certificate bundle is a group of CA certificates (either root or/and intermediate) utilized by a trust store.
Locate the Trust Stores service and create a new Trust Store. Upload your Certificate Authority (CA) bundle, along with any optional revocation lists.
Provide the necessary details, such as Trust Store Name, S3 bucket URI, and choose the version for the S3 object
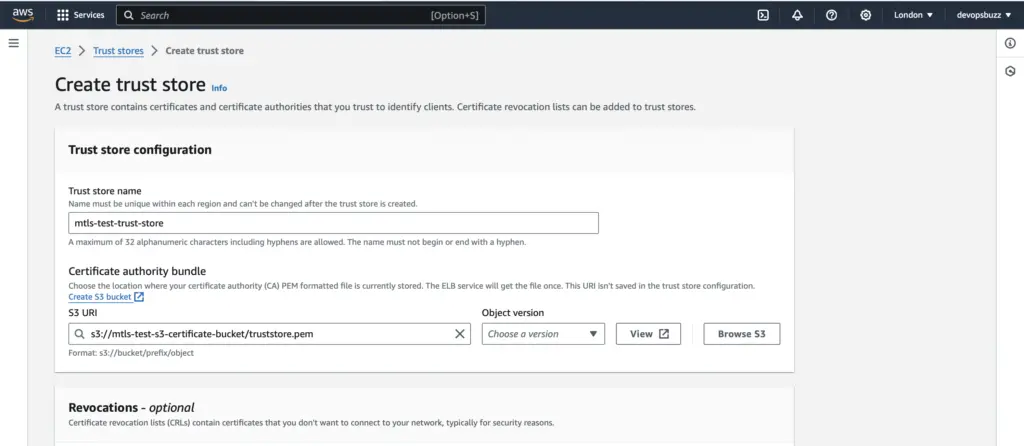
Click on Create trust store and verify the newly created Trust Store
Now follow the same process of creating Load Balancer as mentioned above for Passthrough option
As soon as you choose Verify with trust store option; it will enable a couple of more options; Client certificate handling which decides how the load balancer responds when a client certificate expires and an option to choose Trust store
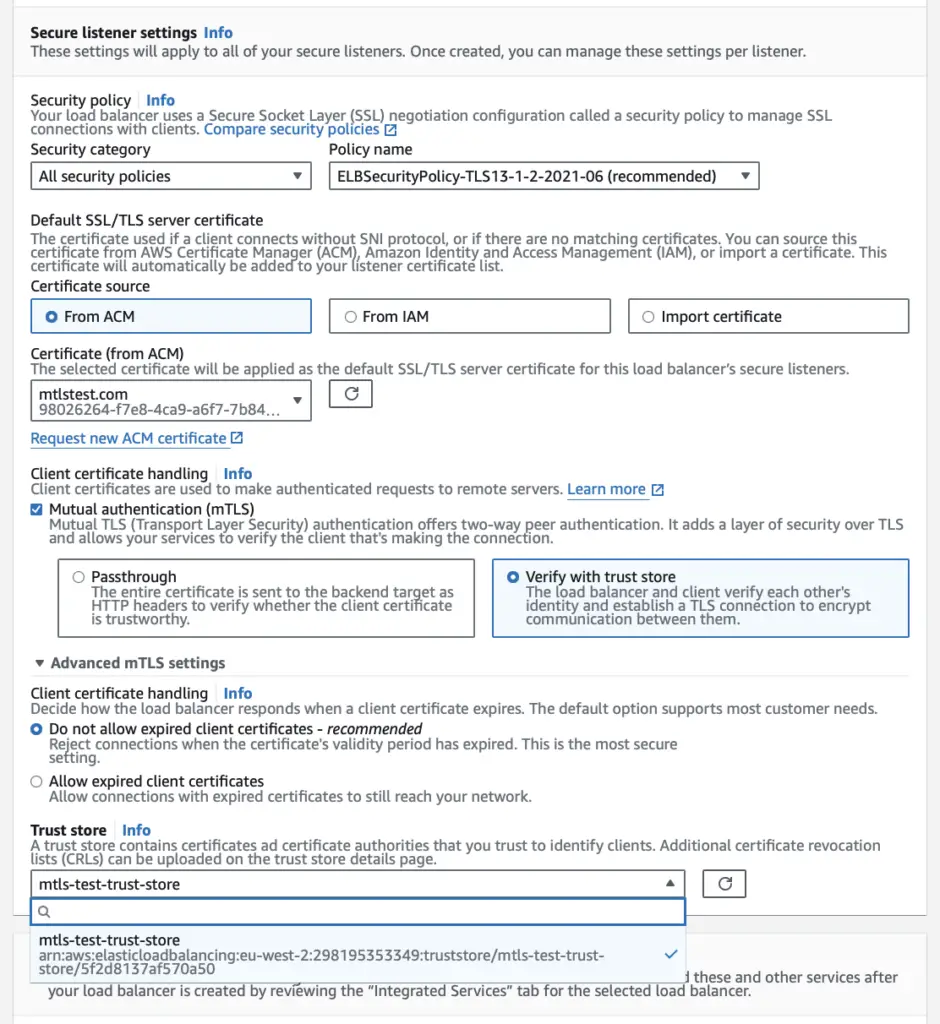
Click on Create Load Balancer
Verify the newly created Load Balancer details
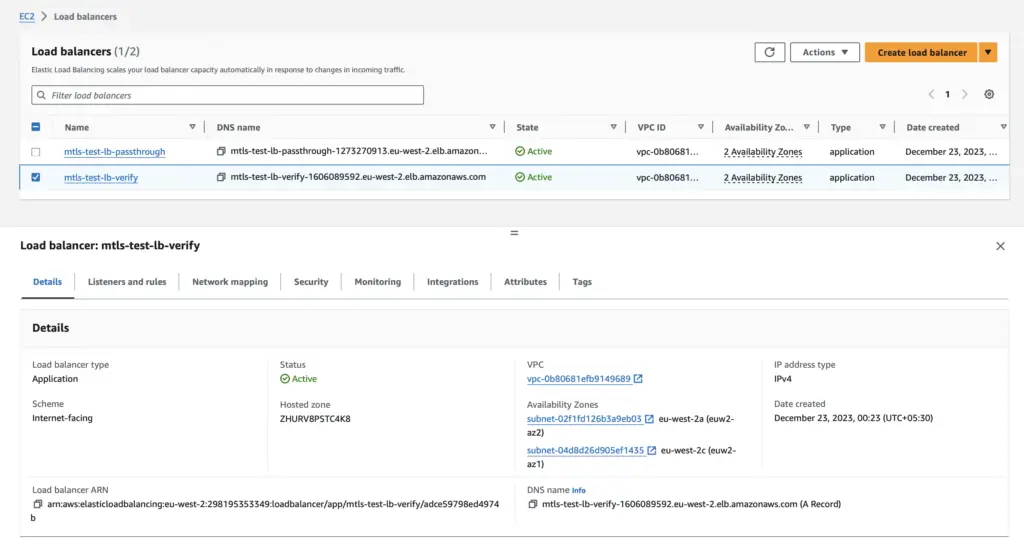
And verify Listeners and Rules
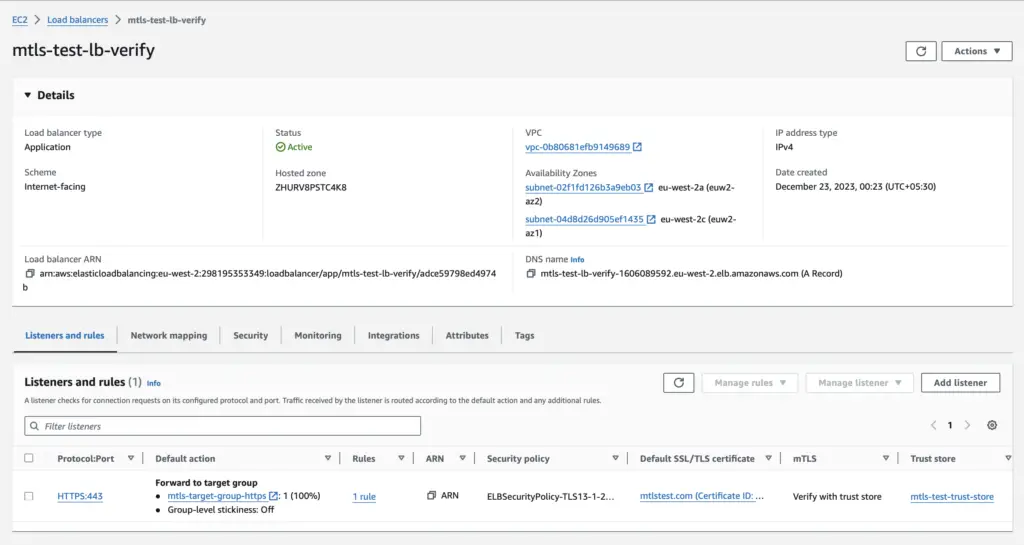
This is how you configure mTLS on ALB. AWS has simplified this previously intricate process, making it straightforward. Select the appropriate option based on your requirements.
Let’s attempt to verify the mTLS using OpenSSL. I’ll generate a self-signed certificate, but even for testing or proof of concept, you can always use a trusted certificate authority. Consider obtaining a valid TLS certificate from sites like ZeroSSL, Let’s Encrypt, etc
1. Generate Root Certificate Authority (CA) Key and Certificate
Generate a private key for the Root CA (You can use 4096 bit key which does provide a reasonable increase in strength over a 2048 bit key)
$ openssl genpkey -algorithm RSA -out rootCA.key
..........................................+++
..................+++Generate a Root CA certificate:
$ openssl req -new -x509 -key rootCA.key -out rootCA.pem -days 30 -subj "/C=GB/ST=State/L=London/O=devopsbuzz/CN=mtlstest.com" -extensions v3_ca -config <(echo "[req]"; echo "distinguished_name=req"; echo "[v3_ca]"; echo "keyUsage=keyCertSign,cRLSign"; echo "basicConstraints = CA:TRUE";)2. Generate Client Key and Certificate Signing Request (CSR)
Generate a private key for the client:
$ openssl genpkey -algorithm RSA -out client.key
.........................................................................+++
.......+++Generate a CSR for the client:
$ openssl req -new -key client.key -out client.csr -subj "/C=GB/ST=State/L=London/O=devopsbuzz/CN=Client"3. Sign Client CSR with Root CA
Sign the client CSR using the Root CA certificate and private key:
$ openssl x509 -req -in client.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out client.pem -days 50 -sha256 -extfile <(echo "keyUsage = nonRepudiation, digitalSignature, keyEncipherment"; echo "extendedKeyUsage = clientAuth"; echo "basicConstraints = CA:FALSE")
Signature ok
subject=/C=GB/ST=State/L=London/O=devopsbuzz/CN=Client
Getting CA Private Key4. Verify Certificates
To verify the client certificate:
$ openssl verify -CAfile rootCA.pem client.pem
client.pem: OK5. Copy the root certificate
Copy the existing root CA public key to a new truststore.pem file name for further clarity on which file is being used by ALB as the trust store
$ cp rootCA.pem truststore.pemThen upload this truststore.pem into the S3 bucket and configure mTLS on ALB as per given instructions
Verify the application on ALB without providing client certificate
$ curl -vv -k https://mtls-test-lb-verify-1606089592.eu-west-2.elb.amazonaws.com/
* Trying 3.9.222.171:443...
* Connected to mtls-test-lb-verify-1606089592.eu-west-2.elb.amazonaws.com (3.9.222.171) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /etc/ssl/cert.pem
* CApath: none
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server key exchange (12):
* TLSv1.2 (IN), TLS handshake, Request CERT (13):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Certificate (11):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* LibreSSL SSL_connect: Connection reset by peer in connection to mtls-test-lb-verify-1606089592.eu-west-2.elb.amazonaws.com:443
* Closing connection 0
curl: (35) LibreSSL SSL_connect: Connection reset by peer in connection to mtls-test-lb-verify-1606089592.eu-west-2.elb.amazonaws.com:443 This didn’t work as expected !
We have to use -k (–insecure) option since we are using self-signed certificate, you can remove this parameter when you are using Trusted CA certified certificate.
Verify the application on ALB by providing the client certificate
$ curl --key client.key --cert client.pem -vvv -k https://mtls-test-lb-verify-1606089592.eu-west-2.elb.amazonaws.com/
* Trying 3.9.222.171:443...
* Connected to mtls-test-lb-verify-1606089592.eu-west-2.elb.amazonaws.com (3.9.222.171) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /etc/ssl/cert.pem
* CApath: none
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server key exchange (12):
* TLSv1.2 (IN), TLS handshake, Request CERT (13):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Certificate (11):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS handshake, CERT verify (15):
* TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* TLSv1.2 (IN), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / ECDHE-RSA-AES128-GCM-SHA256
* ALPN, server accepted to use h2
* Server certificate:
* subject: C=GB; ST=State; L=London; O=devopsbuzz; CN=mtlstest.com
* start date: Dec 22 18:35:41 2023 GMT
* expire date: Jan 21 18:35:41 2024 GMT
* issuer: C=GB; ST=State; L=London; O=devopsbuzz; CN=mtlstest.com
* SSL certificate verify result: self signed certificate (18), continuing anyway.
* Using HTTP2, server supports multi-use
* Connection state changed (HTTP/2 confirmed)
* Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0
* Using Stream ID: 1 (easy handle 0x125013c00)
> GET / HTTP/2
> Host: mtls-test-lb-verify-1606089592.eu-west-2.elb.amazonaws.com
> user-agent: curl/7.77.0
> accept: */*
>
* Connection state changed (MAX_CONCURRENT_STREAMS == 128)!
< HTTP/2 200
< date: Fri, 22 Dec 2023 23:46:01 GMT
< content-type: text/html
< content-length: 615
< server: nginx/1.24.0
< last-modified: Fri, 13 Oct 2023 13:33:26 GMT
< etag: "65294726-267"
< accept-ranges: bytes
<
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
* Connection #0 to host mtls-test-lb-verify-1606089592.eu-west-2.elb.amazonaws.com left intactVoila!, we are able to access our Nginx webpage by successfully authenticating with our client certificate.
Now, lets try the same Mutual authentication through Browser
Try accessing the ALB passthrough url – It will prompt for the certificate
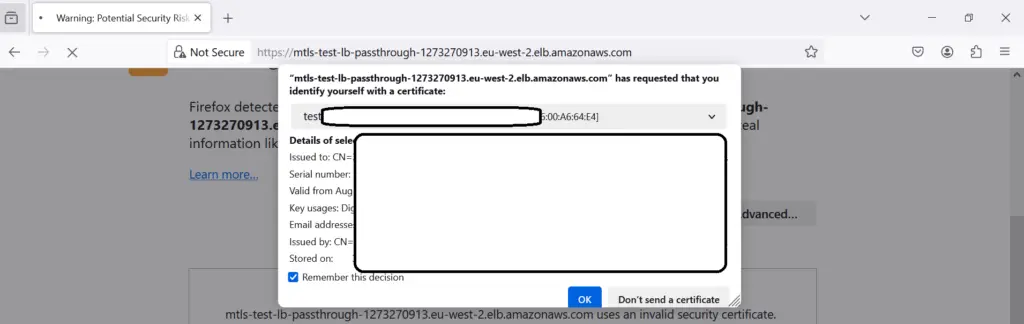
I just used one of my old certificate, which was signed by another CA – so ideally this shouldn’t work 🙂
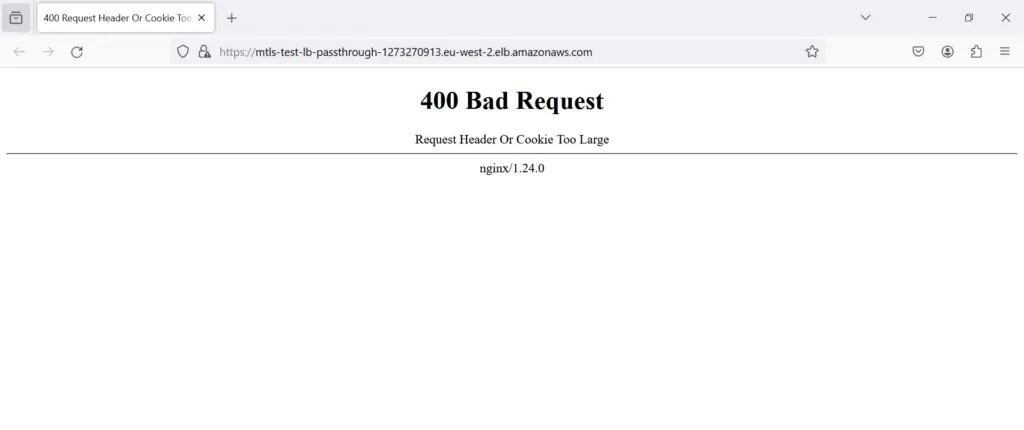
It didn’t work as expected.
So, now lets move forward and Import the Client certificate to the browsers.
If you’re uncertain about generating a .pfx file for browsers and the process of importing it, please refer to this section of our mtls article
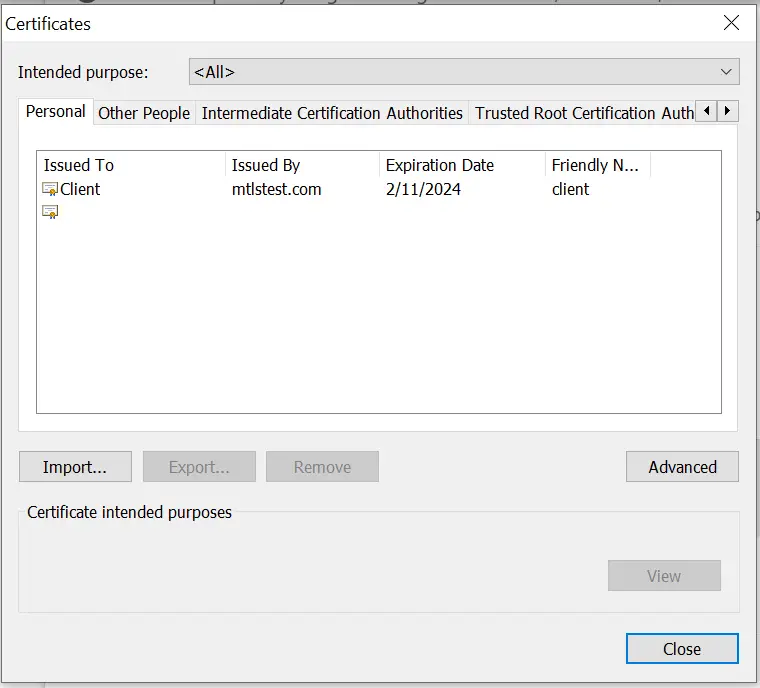
Verify the imported certificate
Let’s try again to access ALB passtrhough URL and this time select the correct client certificate
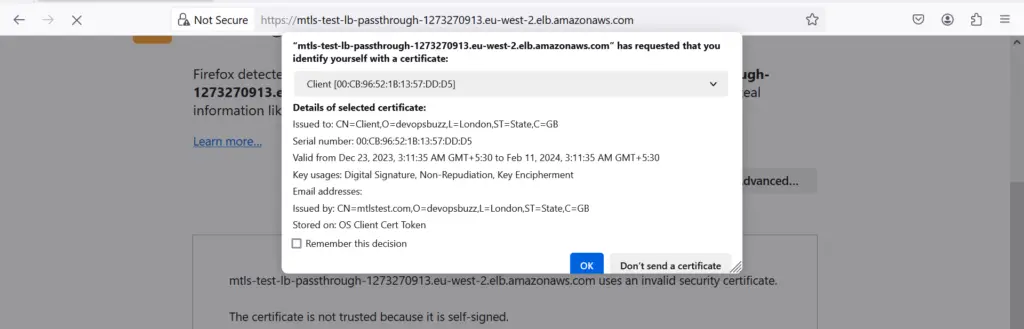
After selecting the appropriate Client certificate, click on OK
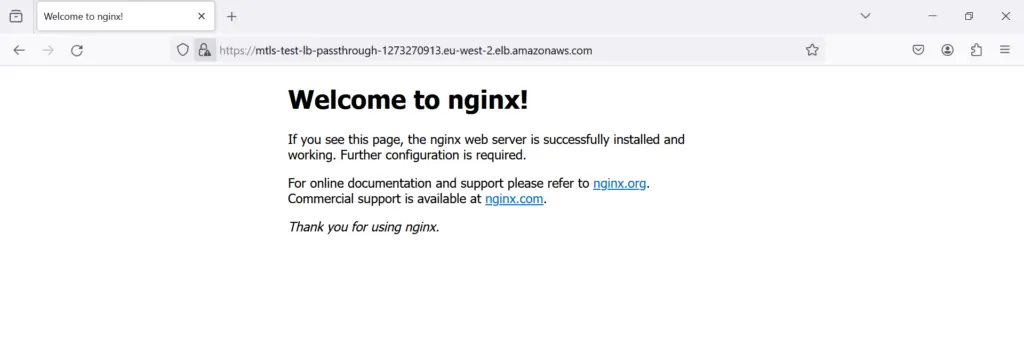
Bingo! Its working as expected.
Now, lets try the other ALB verify url and select the same client certificate.
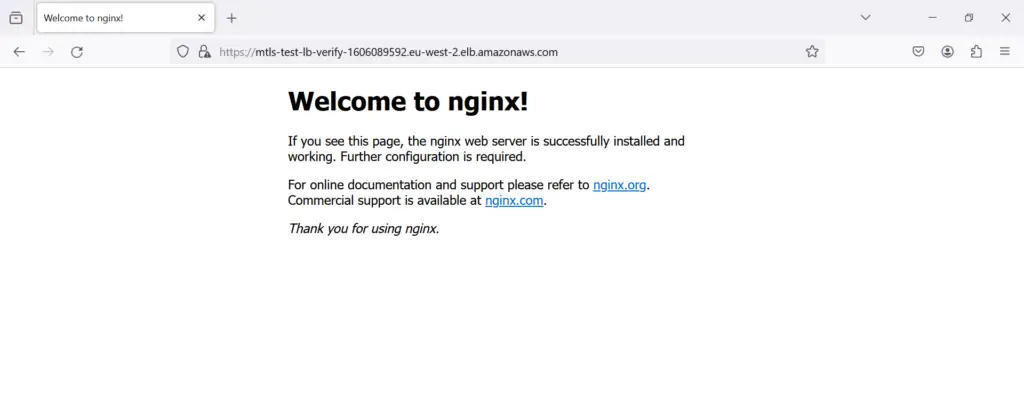
We have successfully validated the Application Load Balancer (ALB) functionality with mutual TLS (mTLS), ensuring proper operation with client certificates as expected.
Security Enhancements with mTLS
Mutual TLS on AWS Application Load Balancers significantly elevates the security profile by enabling bidirectional authentication.

Revocation Checks and Trust Stores
With mTLS support in AWS ALB, checking client certificates against a trust store is now possible. Revocation checks are performed against a Certificate Revocation List (CRL) or using the Online Certificate Status Protocol (OCSP), ensuring no revoked certificates gain access.
For trust store management, I import trusted CA certificates to establish a chain of trust for client authentication. This process is essential for maintaining a secure communication channel.
Smart Certificate Selection
When it comes to security protocols and ciphers, smart selection is key. We can configure the Application Load Balancer to support multiple TLS certificates, and it intelligently selects the appropriate certificate based on the domain name using Server Name Indication (SNI). This adaptability ensures not only secure but also efficient connections by matching the client’s capabilities with the best security standards available.
Custom Security Policies
As part of the security enhancements, AWS ALB now allows you to define custom security policies, giving you more control over ciphers and protocols used during the TLS negotiation process. By having a custom security policy, you can specify which ciphers and protocols are acceptable, ensuring a secure connection between the client and the server and guaranteeing compliance with the specific requirements of the resources behind the load balancer.
Best Practices and Recommendations
When configuring Mutual TLS (mTLS) on AWS Application Load Balancers (ALB), it’s important to follow some best practices to ensure a secure and efficient setup. Here are some of the recommendations:
Firstly, it is essential to ensure that the ALB trusts the correct Certificate Authorities and to rotate certificates regularly to maintain the security of your mTLS setup. Make sure to replace the SSL/TLS certificates before they expire to avoid connection interruptions and potential vulnerabilities.
Next, validate client certificates. When configuring mTLS on ALB, ensure that you only accept certificates issued by a trusted Certificate Authority (CA). This helps only allow authenticated clients to access your backend services, ensuring a high level of security.
Keep client certificates secure at all times. Follow standard security protocols for certificate issuance, transport, storage, and use. Also audit certificate usage regularly to detect any unauthorized accesses.
Additionally, you should enable ALB access logs. Enabling access logs helps you analyze traffic patterns, troubleshoot issues, and maintain compliance. The logs can provide granular details about requests made to your ALB, such as client IP addresses, request paths, response codes, and more.
Moreover, it’s important to plan for high availability and scalability. To ensure that your ALB can handle varying loads and maintain high availability, consider distributing targets across multiple Availability Zones and scaling target groups based on demand.
To achieve optimal performance, take advantage of ALB’s support for multiple TLS/SSL certificates with Server Name Indication (SNI). This allows you to host multiple TLS secured applications, each with its own certificate, behind a single load balancer. In addition, carefully pick the appropriate SSL/TLS policiesthat suit your performance and security needs.
Before fully deploying mTLS, always conduct thorough testing to verify that the ALB rejects unauthorized access, and legitimate traffic flows correctly with minimal latency added.
Lastly, don’t forget about compliance. Make sure your mTLS configurations adhere to relevant industry standards, such as PCI DSS, HIPAA, GDPR, and others. This helps you maintain a secure, reliable, and compliant environment for your clients.
By following these best practices and recommendations, I believe you can effectively manage and maintain mTLS configurations on your AWS ALB to optimize security, performance, and reliability.
Testing and Validation
When setting up mTLS on ALB, it is essential to test, validate, and troubleshoot the configuration and connections effectively. In this section, I will share some techniques, tools, and methodologies for addressing issues during the mTLS and ALB integration process.
Firstly, make sure to test the mTLS connection and handshake by using tools like openssl and curl with the appropriate client certificates and keys. These tools help simulate the interaction between clients and the ALB, allowing you to identify potential issues.
For example, to verify your mTLS connection using openssl, run:
openssl s_client -connect example.com:443 -cert client.crt -key client.key -CAfile ca.crtNext, monitor AWS CloudWatch Logs and ALB access logs to analyze any errors or failed authentication attempts. Check for errors related to certificates, cryptographic protocols, or handshakes that may cause the mTLS connection to fail.
Monitoring, Logging, and Auditing
First, monitoring mTLS connections and performance is crucial. AWS CloudWatch offers various metrics for the Application Load Balancer, enabling you to keep track of its health in real time. These metrics include request counts, latency, and backend connection errors, among others.
To enhance the security aspect, AWS provides Access Logs and Connection Logs for ALB, capturing detailed information about the requests sent to your load balancer.
This data includes the time the request was received, the client’s IP address, latencies, request paths, and server responses. These logs help you analyze traffic patterns and troubleshoot any issues with your load balancer and targets.
For auditing, AWS CloudTrail logs provide an audit trail of all API calls made on your account, including those related to mTLS configurations. By analyzing these logs, you can quickly detect any unauthorized or suspicious activity.
Additionally, AWS Config is another powerful tool to monitor your ALB’s mTLS configuration by recording its changes over time and assessing compliance.
To ensure you get notified about any anomalies, events, or issues related to mTLS connections, I recommend configuring alarms in CloudWatch.
These alarms allow you to set threshold values for specific metrics, and if the thresholds are breached, notifications will be sent through your preferred communication channels.
AWS ALB’s support for mTLS is an excellent addition, and monitoring, logging, and auditing are essential components for maintaining a secure and compliant environment.
Troubleshooting mTLS on ALB
In this section, we will focus on troubleshooting mTLS on AWS ALB, covering common configuration issues, certificate errors, and analyzing access logs for issues.
Common Configuration Issues
Below are some common configuration issues you might encounter:
- Trust store configuration: Ensure you’ve created a new trust store resource and uploaded your Certificate Authority (CA) bundle, as detailed in the AWS documentation.
- Listener Setup: Make sure the listener is correctly configured to verify client certificates, as shown in the AWS blog post.
Certificate Errors and Validation
Certificate-related issues can occur in mTLS configurations. Here are a few possible problems:
- Client Certificate: Verify that clients have valid certificates signed by a trusted CA.
- Server Certificate: Double-check that your application server’s certificate is valid and properly configured.
- Certificate Expiration: Ensure that both client and server certificates are not expired, and always keep them up to date.
- CA Bundle: Make sure the CA bundle uploaded to the ALB trust store is correct and includes all necessary intermediate and root certificates.
Analyzing Access Logs for Issues
To identify issues related to mTLS, you can analyze AWS ALB access logs. These logs provide details about incoming client requests and ALB’s responses. Here’s what to look for:
- Check the TLS negotiation errors in access logs. These errors can indicate issues related to certificate validation, expiration, or revocation.
- Look for 502 Bad Gateway errors, which could signal an issue with the client certificate or TLS handshake.
- Monitor the “ssl_policy” field in the logs to ensure that the desired SSL/TLS security policy is being applied.
Some common challenges and pitfalls during mTLS and ALB deployment include:
- Expired or incorrectly-signed certificates: Ensure that certificates are up-to-date and signed by a trusted certificate authority (CA).
- Incorrect ALB Listener Rules: Configure ALB listener rules to support mTLS and forward traffic to the right target groups.
- Misconfigured target groups: Set up target groups to expect mTLS traffic and inspect client certificates.
- Overlook security group configurations: Security groups must be set to allow ingress on the correct ports and protocols.
- Incompatible cryptographic suites: Both the client and server must support a common set of cryptographic algorithms to establish a secure connection.
To address some of these challenges, consider the following solutions:
- Regularly update and renew certificates to prevent expiration-related issues.
- Implement monitoring or alerting rules on AWS CloudWatch to detect potential issues automatically.
- Employ automated testing pipelines for certificate management and mTLS configuration.
By addressing common challenges and employing the right tools and techniques, you can ensure a seamless and secure mTLS integration for your AWS Application Load Balancer.
By staying vigilant and keeping these troubleshooting tips in mind, you can ensure a smooth experience while implementing mTLS on AWS ALB.

Performance and Compatibility Considerations
Impact on Latency and Throughput
With the introduction of Mutual TLS (mTLS) support in AWS Application Load Balancer (ALB), there are some considerations to keep in mind regarding performance.
First, it’s essential to understand the added cryptographic overhead when enabling mTLS. Although modern browsers like Chrome, Firefox, Edge, and Safari efficiently handle TLS connections, the additional certificates and validation process might slightly impact latency and throughput.
However, AWS ALB provides a Passthrough option which enables the load balancer to forward the client certificate to the backend application using HTTP headers, thus reducing some of the associated overheads.
Browser and Client Compatibility
Although most modern browsers support mTLS, it’s crucial to highlight the compatibility and behavior of different browsers during the configuration process.
For instance, older versions of Internet Explorer might exhibit compatibility issues; hence, it’s essential to ensure that the ALB settings and client certificates are compatible with the target audience’s most commonly used browsers.
In the AWS ALB mTLS configuration, the support for different certificate types and signature algorithms is extensive, including X.509v3 certificates, RSA and ECDSA public keys, and various SHA signatures.
Ensuring that your certificate selections are compatible with your clients’ browsers will keep the overall experience smooth and hassle-free.
By carefully considering the performance and compatibility implications during the configuration process, you can optimize the performance and security of your backend applications while ensuring an excellent user experience for your clients.
Frequently Asked Questions
What is the difference between x509 and PEM certificate?
x509 is a standard for public key certificates, whereas PEM (Privacy Enhanced Mail) is a format for encoding and storing x509 certificates. x509 certificates can be stored in different formats such as DER (binary) and PEM (Base64 ASCII). PEM is used for encoding x509 certificates in a text-based format, making it easier to manage and exchange certificates.
What is the difference between X.509v1 vs X.509v3?
X.509 is a standard defining the format of public-key certificates, which are used for various security applications, including TLS/SSL for securing web communications. X.509v1 and X.509v3 refer to different versions of this standard, and they have key differences in terms of features and capabilities.
While X.509v1 provides the basic structure for public-key certificates, X.509v3 enhances the standard by introducing key extensions such as Key Usage and Subject Alternative Name.
X.509v3 certificates offer a more flexible and extensible framework, providing additional features and capabilities crucial for modern security requirements. Most certificates used today, including those for SSL/TLS, are based on the X.509v3 standard.
How do you enable mTLS on an AWS Network Load Balancer?
To enable mTLS on an AWS Network Load Balancer, follow my previous article, I discussed configuring mTLS on an AWS Network Load Balancer.
What are the differences between TLS termination and mTLS on AWS ALB?
TLS termination is the process of decrypting incoming TLS traffic at the load balancer level before forwarding it to backend servers. It allows the ALB to perform actions on the traffic, like inspecting it for routing and security purposes.
mTLS, on the other hand, is an extended version of TLS that ensures both client and server authenticate each other using certificates during the TLS handshake. mTLS on AWS ALB involves the load balancer verifying client certificates, ensuring that only clients with valid certificates can communicate with the backend services.
How does mTLS authentication work with AWS ALB when integrated with Amazon ECS applications?
When mTLS is enabled on an AWS Application Load Balancer, the ALB receives the client certificate in the handshake, establishes a TLS connection, and then sends the certificate information in HTTPS headers to the target application. An ECS application can access the certificate information from the headers and can verify the client certificate chain to authenticate the client.
How much would be the charge for using mTLS on AWS ALB?
The cost of mTLS on AWS ALB depends on the number of active connections, the amount of data transferred, and the AWS region where the ALB is deployed. There is no direct cost for enabling mTLS, but additional processing for the mTLS handshake may affect your cost based on the number of new connections established. For a detailed pricing breakdown, refer to the official AWS pricing page for ALB.
Is it possible to use AWS WAF in conjunction with mTLS on an AWS Application Load Balancer?
Yes, you can use AWS WAF (Web Application Firewall) in conjunction with mTLS on an AWS Application Load Balancer. The ALB will handle mTLS authentication, and the WAF will protect your application from common web-based threats.
How to configure mutual TLS authentication for Amazon API Gateway
To configure mTLS authentication on Amazon API Gateway, follow the official documentation, which provides detailed steps for setting up a custom domain, importing a CA certificate, and configuring mTLS on an API Gateway stage.
Are there any compliance considerations or regulatory requirements to consider when implementing mTLS on ALB?
When implementing mTLS on ALB, ensure that you adhere to your organization’s security and compliance policies and any applicable regulatory requirements. These may involve using specific types of certificates, following encryption standards, or satisfying data protection regulations.
It’s important to consider compliance and regulatory requirements like FIPS 140-3, which mandates the use of approved cryptographic modules. Ensure that your mTLS setup adheres to the specific standards and laws relevant to your industry and the nature of your data.
It is essential to consult with your organization’s security and compliance experts to understand and achieve adherence to any specific security guidelines.
Can Amazon EKS clusters be configured to use mTLS ?
Amazon EKS clusters can be configured to work with an AWS Application Load Balancer using mTLS. You will need to configure the AWS ALB for mTLS and define matching settings within your Kubernetes Ingress objects or service annotations in the EKS cluster.
If you are using aws-load-balancer-controller, there is an ongoing issue that has been acknowledged, and once resolved, the alb controller will inherently support mTLS.
This article describes how to configure mutual TLS for applications running on an Amazon Elastic Kubernetes Service (Amazon EKS) cluster by using an NGINX ingress controller. You can enable built-in mutual TLS features for the NGINX ingress controller by annotating the ingress resource.
How does mTLS impact performance, latency, throughput, scalability, and cost within my AWS infrastructure and ALB environment?
Enabling mTLS on your AWS ALB can impact performance and latency due to the additional steps involved in the mTLS handshake. This may slightly increase connection times and decrease throughput.
However, the impact on scalability and overall cost depends on various factors, including the number of new connections and the volume of data transfer.
How often should I review, update, or modify my mTLS configurations, certificates, settings, and policies on ALB to ensure security, compliance, and optimal performance?
Regularly reviewing and updating your mTLS configurations and certificates is vital for maintaining security and compliance. Factors affecting the review frequency include your organization’s security policies, regulatory requirements, and the certificate validity period.
Additionally, staying current on AWS ALB updates and best practices will help ensure that your mTLS implementation remains secure and performs optimally.
Wrapping Up
I trust that this article has provided valuable insights into the implementation of mutual TLS (mTLS) on AWS Application Load Balancer.
I hope you found the step-by-step guidance and practical demonstrations helpful in leveraging the enhanced security features of mTLS within your AWS environment.
Thank you for your readership, and may your applications benefit from the strengthened security measures offered by mTLS on AWS ALB.


For anyone dealing with AWS ALB and considering Mutual TLS, I found this step-by-step guide incredibly helpful. Sharing it with my team and network! #AWS #DevOps
Great walkthrough on implementing mTLS on AWS ALB! The step-by-step guide and detailed explanations are invaluable for anyone looking to enhance the security of their applications. Kudos to the author!
Wow, such detailed instructions for configuring mTLS on ALB. Simply amazing